

Our Cybersecurity Risk Assessment services are a cornerstone of proactive defense in the cyber age, offering organizations a comprehensive and strategic approach to identifying, analyzing and mitigating potential cybersecurity threats and regulatory challenges. Our blue team of security operations, center analysts and governance risk compliance analysts is complimented by having a dedicated red team.
Our assessments go beyond surface-level interviews by analyzing and identifying gaps between your security policies and technology footprint. We employ rigorous methodology based on NIST to ensure we capture the highest impact risks across all of your assets.
Our risk assessments help you map out your compliance posture, providing clear documentation and evidence of adherence to regulatory requirements set forth by bodies such as the SEC and FCA.
Every risk assessment report includes specific, actionable risk remediation recommendations that are prioritized, allowing you to focus on most critical issues first, optimizing resource allocation and enhancing security effecitveness.
Insights gained from our risk assessments are seamlessly integrated into our Cybersecurity Dashboard, providing organizations with an accessible, centralized view of their risk register, facilitating ongoing monitoring, management and mitigation of risks.
We help organizations understand their attack surface and defense-in-depth security posture by emulating a malicious adversary attempting to hack into their organization by exploiting vulnerabilities across their cloud, network and server infrastructure.
You don't want to invite just anyone to hack into your organization. You can trust the quality and expertise from our team of full-time US and UK employees holding the highest industry certifications: CISSP, CRTP, OSCP, OSWP, OSWE, Security+, PenTest+, and CNVP.
Our team offers unparalleled insight into the latest hacking techniques employed by notorious groups such as LockBit. We build and share cutting-edge tools like Legion, a semi-automated penetration testing framework utilized by hundreds of other security firms, and provide the latest advanced defense strategies available to protect you from costly incidents.
Following each penetration test, we provide a detailed due diligence report that not only outlines discovered vulnerabilities, but also offers prioritized, actionable recommendations for mitigating these risks. When imported into our Cybersecurity Dashboard, organizations are empowered to track the remediations of all their risks in one centralized view.
Our testing services are designed to help organizations navigate and comply with stringent industry regulations from the SEC, FCA, DORA and NYDFS 23 NYCRR 500. Leveraging corroborating security testing frameworks such as MITRE ATT&CK, PTEST, and NIST SP800-115 allows our team to provide comprehensive insight into your organizations security posture from the perspective of a hacker.
Our Social Engineering services transcend traditional phishing tests by deploying a suite of sophisticated, real-world tactics designed to evade your security defenses and gain a foothold into your organization through its staff. Our approach tests your incident response capabilities by mirroring the cutting-edge techniques employed by today's cyber adversaries, including leveraging generative AI voice impersonation.
We employ a broad arsenal of social engineering techniques, including pretexting, impersonation, domain typo-squatting, and cutting-edge methods like generative AI voice impersonation. These tactics delve much deeper than standard email phishing tests, challenging your employees with the type of sophisticated attacks used by real-world cybercriminals, thus providing a more accurate measure of your organization's security posture through social engineering.
The insights gained from our social engineering engagements serve as critical drills for your incident response teams. This method significantly improves your organization's defense-in-depth strategy and incident response capabilities, preparing your team for the nuances of real-world cyber threats.
All incident response and security hardening recommendations from our social engineering testing are integrated into our Panoptix Cybersecurity Dashboard. This enables your organization to prioritize suggested security enhancements and improve your overall security posture against the sophisticated social engineering attacks of tomorrow.
Cybersecurity is crucial to the financial services industry due to the sensitive nature of the data involved and the potential financial implications of a breach. Financial institutions process the personal and financial information of millions of customers, making them prime targets for cybercriminals. In 2022, the finance industry averaged a cost of $6.1M per data breach. However, organizations with a well-designed Incident Response Plan reduced data breach costs by about 60%. Social engineering remains a top vector for gaining a foothold, with the median amount stolen increasing to $50,000.
Abacus Group can help protect your firm against evolving threats and compliance demands.
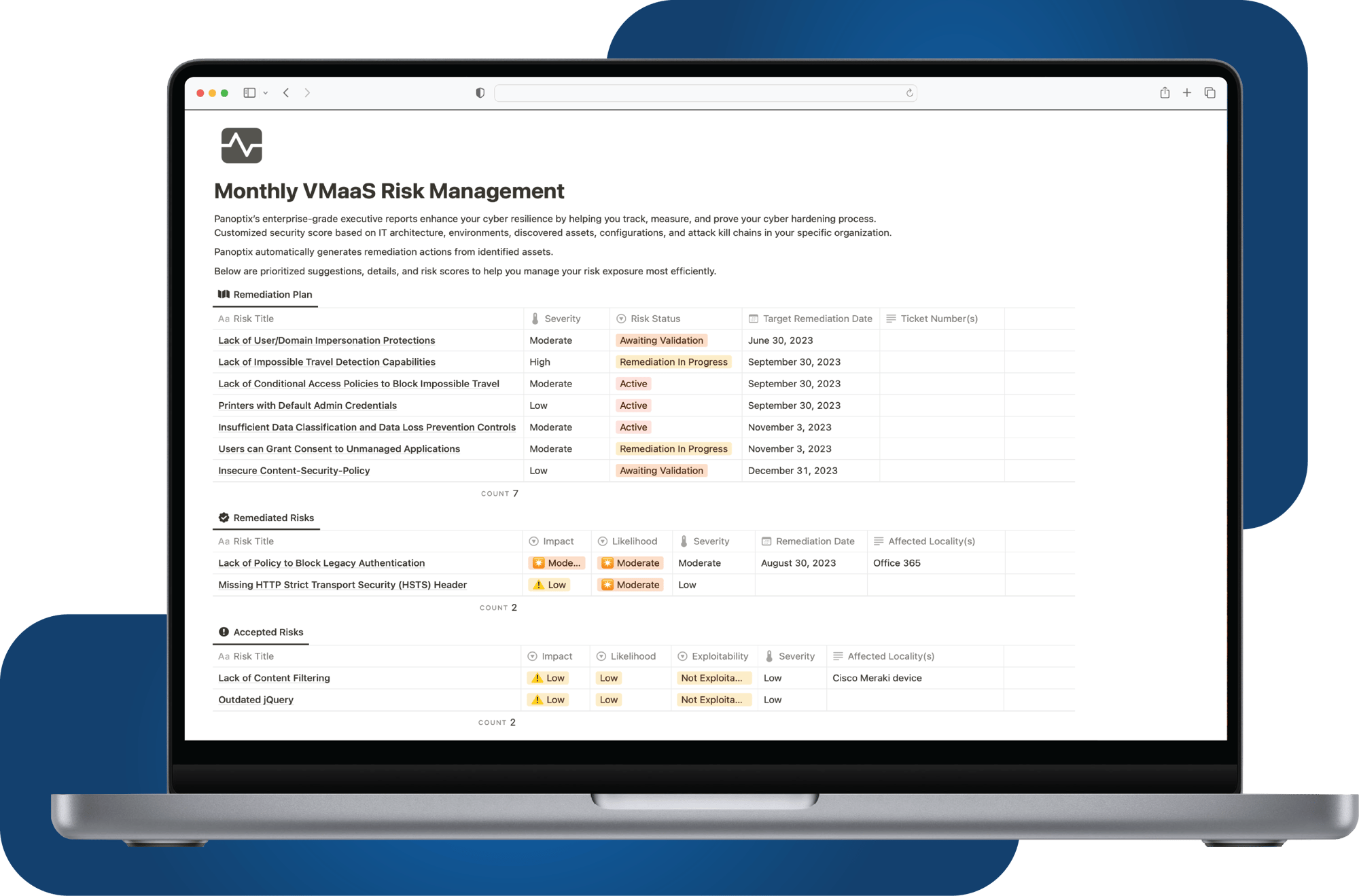
We provide a transparent cybersecurity and risk management dashboard, empowering you to continuously monitor, measure and improve your organization's security posture. Data from our cybersecurity testing services automatically funnels into your dashboard, allowing you to track your cybersecurity efforts in one place in realtime.